Are You Vulnerable to an Internal Content Breach?
How to quickly detect and react to abnormal user behavior
Most organizations generally prepare for security threats such as: system attacks, stolen malware, IDs and passwords, or problems with access control. However, recently internal threats have become a growing concern within many organizations. Users with appropriate access are searching, viewing, and editing content from their company's Enterprise Content Management systems, with no business reason to do so, including HR, legal, and medical data. And it's not only employees with access to this content - it can also be partners, contractors, and clients (both local and external). Furthermore, in some instances employee credentials may be compromised and used by another authorized user.
For Most Organizations, Content is One of Their Most Valuable Assets
If you think about industries like pharmaceutical, finance, and legal, the majority of their output is data. But if you also consider industries such as engineering and retail, although data may not be their major output, it is still incredibly valuable to them. Data can be stored in multiple locations - it can be stored on an internal infrastructure, on a private cloud, on a public cloud, or even a mixture of the three. It can also be on multiple content management applications such as IBM FileNet, IBM DataCap, IBM Content Manager OnDemand (CMOD) and SharePoint.
How to Protect Against a Content Breach
In order to protect your data against a content breach, you must be able to look at what a user is doing within your systems and define baselines on performance and usage. You must be able to identify and resolve problems proactively, such as unusual user activity. For example, a Pharmaceutical company may be interested in what their users were exporting outside of working hours. Alternatively, an organization with a potential Human Resources breach may be interested in whether or not administrators were accessing the HR data from an inappropriate interface.
There are several steps that you must take to properly to ensure system’s security and operational performance:
- Behavioral Security: Be aware of what users are doing and how they’re using content - make sure they are acting in a compliant way!
- Audits: Really understanding what your users are doing on the system allows simplification of report production from a compliance and security standpoint.
- Performance Analytics: Ensure your content platform is humming along. As you look at what users are doing and how the system is performing for them, you can really provide deep analysis of all of your data.
- Application Adoption: Understand how users are interacting with the different interfaces and whether they're using them appropriately.
- Capacity Planning: If you know you’re going to have additional users accessing the system over a period of time, you must plan appropriately.
- Upgrade Planning: Look at the baseline of how your system is performing both before and after the upgrade to ensure the performance is improving.
Content Access Breaches
The biggest threat is from "authorized" insiders
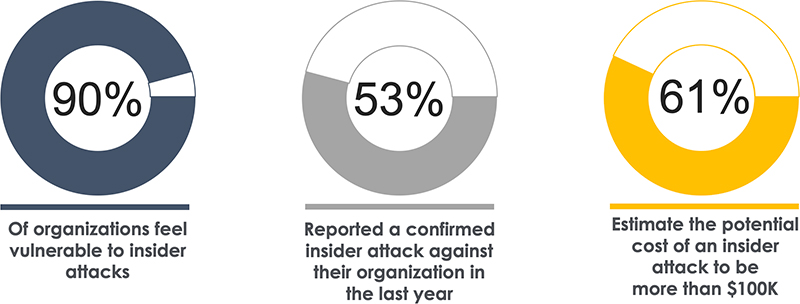
Figure 1. Source: Cybersecurity Insiders, 2019 Insider Threat Report
Real Time Monitoring of Your Content
enChoice is an award-winning IBM Gold Partner, and we’ve been providing Managed Services support to customers since 1994. Currently sitting at greater than 500 IBM ECM customers worldwide, we are hitting just about every sector of the market. Our Managed Services Customer Satisfaction Rating has consistently maintained a 9.5 out of 10 or better since 2003.
One component of our Managed Services offering includes Real Time Monitoring. Content Security Breach Protection is a functional add-on to our content Real Time Monitoring solution, which enables you to:
- See what users are doing within your systems
- Define baselines on performance and usage
- Flag unusual user behavior and performance
- Automatically resolve problems (if required)
The Process of Protecting Your Content
The first step to monitoring and protecting your content is gathering your data from multiple applications, testing your system, and then pulling the data out. Next, we help you identify what end users are doing on your system when they’re interacting with the back-end interfaces and content management systems. We can collect all of the data and place it within the data store, which allows us to do an analysis on the data. We look at how your systems are being used, how it's performing for the end users, and also what those end users are doing. This gives us greater insight into your overall Enterprise Content Management platform.
enChoice’s Real Time Monitoring solution works on multiple client applications - standard Explorer, iPad, or mobile phone. Once you have all of this information we can then help you do something with it. For example, you might want to disable a user based on unusual activity, or restart a server based on poor performance.
Learn More About Breach Protection
If you are looking to learn more about how to quickly detect and react to abnormal user behavior from your content-based applications, such as a large number of asset downloads or exports, inappropriate user account access and/or content access from suspicious locations, watch this 15-minute recorded webinar or contact enChoice for more information on Managed Services.
About the Author
 |
Kieran Fox is a Subject Matter Expert who has worked within the Enterprise Content Management (ECM) industry for over 20 years and has successfully filled roles in pre-sales, professional services and sales. His experience in multiple roles has provided him with an in-depth knowledge of ECM implementations at his clients, their content access requirements and the skill set to deliver security detection solutions to best meet these requirements.
|